28 Ways to Secure WordPress Website

Hallo all, I’ve jst received this
“If you have some time, feel free to have a look at it. If you find it
useful/helpful to your visitors, don’t hesitate to mention in your
blog the help the WordPress community. That would be much appreciated”
by email from john by hostingfacts.com, and appreciating his article and invite, I report his entire article and invite you all to visit his wondwefull site :
in witch you can find many interesting and very usefull articles. All links redirects to his site.
Don’t want your WordPress site to get hacked? Tighten up your security.
I’ve had my site hacked twice. Neither was a particularly fun experience.
In short, getting your site hacked = spending your whole day trying to fix things that you don’t entirely understand.
And that’s provided that the hack wasn’t of a deep-cutting variety.
Luckily for me, patching a few things and changing my web host did the trick and fixed everything. But not everyone gets off that easily. For instance, I have a friend who not only got his site hacked, but then also lost his whole domain as a result of it.I guess the thing I’m trying to say is this:
WordPress site hacking is much more common than we’d like it to be, and it’s steadily on the rise. There was over 81,000 reported hacked sites in 2009, then 98k, 144k, and 170k in subsequent years.
Then, in 2014 we all lost count with one massive report after another. Literally hundreds of thousands of WordPress websites are taken advantage of every year, and possibly millions remain vulnerable.
… But there’s an elephant in the room:
“Why would anyone hack my site?” – you ask
Let’s be clear. Your site is likely not special. Unless your firm’s name is CNN.
The fact is that most – or the great majority, rather – of attacks are automated. This means that various bots (pieces of software) developed by hackers crawl the web and look for vulnerable sites.
Then if they’re successful, the site gets added to the hacker’s portfolio, so to speak, and can be used for various purposes.
In other words, your site by itself is no special, but 10,000 sites just like yours is pure gold for a hacker. Such a network of hacked sites can be used for things like black hat SEO, mass email sending, database scraping (to get your users’ personal info), and so on.
You really shouldn’t feel overly safe just because/if you run a relatively small website.
Hackers don’t discriminate.
Now, WordPress security doesn’t happen automatically. Even though WordPress is an awesome platform, and a hugely popular one, it does have its problems. More so, its popularity contributes to the problems significantly!
Just think about it, if you’re a hacker, you’re not going to try breaking some obscure CMS system. Instead, you’re going after the most popular one out there, just so you can gain access to potentially the biggest number of websites.
All this means that as a WordPress user, you should take care of at least the most basic security measures, just to make sure that you can sleep well, and that you won’t find your website under hackers’ control in the morning.
Okay, let’s get to the good stuff! Here’s everything you need to know about securing your WordPress blog:
BEGINNER TIER
- Securing Administrator account
- Using Editor account for content work
- Strengthening WordPress passwords
- Limiting login attempts
- Securing your own PC
- Updating WordPress automatically
- Updating plugins regularly
- Taking backups of your blog/site
- Choosing legitimate web host for WordPress
- Downloading plugins/themes from well known sources
ADVANCED TIER
- Deleting plugins you don’t use (be careful, though)
- Reducing the overall number of plugins (some can be replaced)
- Installing security plugin (some well-known plugins)
- Protecting WordPress from brute force attacks
- Using CloudFlare
- Monitoring for Malware
- Performing a theme check
- Blocking pingbacks and trackbacks
“THE BEGINNER TIER” of WordPress security
This is your absolute must-do list:
1. Secure your Administrator account
Whatever you do, please don’t use an obvious login/username for your main Administrator account, like “admin” for example.
This is waaaaay too easy to guess. Instead, go with something fun, like “master-commander-45”.
The usernames in WordPress can’t be changed once set during install. So here’s what you do:
- Create a new user account in Users > Add New. Assign it to the Administrator role:
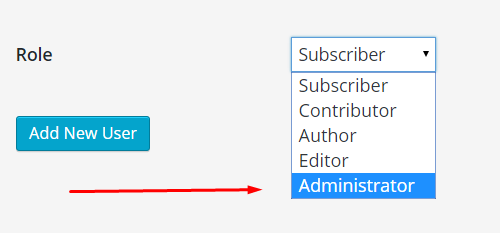
- Delete your original Administrator account (also in Users).
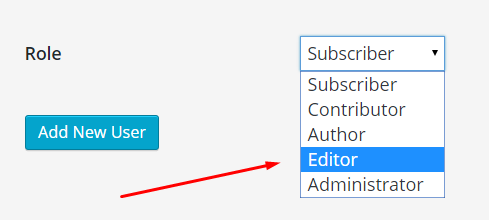
2. Use an Editor account for content work
Using your main Administrator account for editing/publishing work (or when working with content in general) can be risky. Especially if you’re using Wi-Fi at a cafe or something.
Instead, create an Editor account for all content work you do. Again, make the login non-obvious. Do this in Users > Add New.
3. Use secure passwords
Please … I beg of you … don’t use passwords that are easy to guess. Like the most commonly used passwords, or anything that’s a combination of common words (e.g. JohnSmith1).
Instead, follow this path:
- Craft one, just one, ultra secure password for yourself. Follow this guide.
- Sign up to LastPass (it’s free) and set that ultra secure password as your main “vault password.”
- Then, use LastPass to generate safe passwords for everything going on with your site.
Additionally, force the people who also have access to your site to do the same.
4. Limit login attempts
Password guessing is a real threat. Basically, a bot, or even a human, can make multiple attempts at guessing your login/password combinations until they get it right. They may not succeed in 10-20 attempts. But if you’re using a mid-complex password, then the 100,000th attempt can be successful.
Solution? Limit the possible login attempts with this plugin.

5. Secure your own machine
Apart from making your site itself secure, you also need to take care of the computers you’re using to access the site.
There are all kinds of viruses out there. Starting from simple key loggers that will pay close attention to your keystrokes and then try recreating your login and password, to direct FTP-based bots that look for open FTP connections and then upload a hacked file straight to your server.
The solution is simple. Take care of your computer. Use good anti virus software.
6. Update WordPress regularly
Updating WordPress is one of those things that everyone knows they need to be doing, but we still somehow end up forgetting about it. So let me tell you why it is, indeed, crucial.
A detailed change log goes alongside every new release of WordPress. In that change log, every bug that’s been fixed is listed. In other words, it’s a manual for hackers who want to target older versions of WordPress.
How serious this can be? Well, last year, the WordPress guys announced that all versions prior to 3.9.2 were vulnerable to cross-site scripting hacks. Around 86% of all WordPress sites were vulnerable at the time.
And a bit more recently, the Sucuri guys detected a malware campaign already in progress.
Luckily for us, the solution is very simple most of the time … just enable auto-updates for your WordPress site, or always perform an update manually as soon as you see a notification like this:
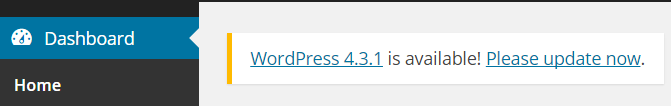
7. Update plugins regularly
When it comes to updates, it’s not only WordPress itself that needs to be kept up to date. The same thing goes for the plugins you’re using.
And the consequences can be quite serious if you neglect this.
For example, a while ago, there was the big MailPoet issue.
(MailPoet is a popular email marketing plugin – you can use it to send email newsletters to your list of contacts directly through your WordPress blog.)
The problem was that a bug in MailPoet enabled hackers to upload PHP executable files to your web server, and take control of the site entirely. Even PCWorld wrote about this! 50,000 sites got hacked.
Lesson? Always update your plugins as soon as a notification pops up. You just don’t know when a new vulnerability gets discovered and then fixed by a subsequent update.
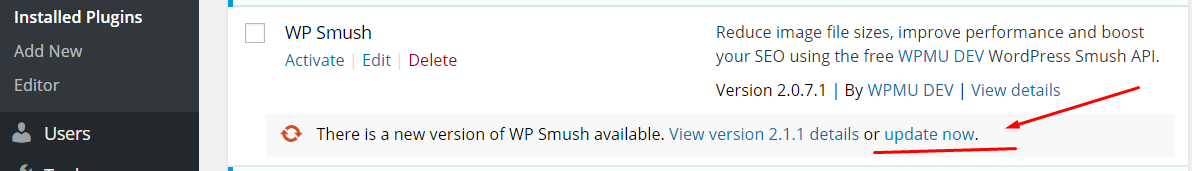
If you miss the mark, you might give the bad guys enough time to successfully attack your site.
8. Back up your site regularly
Granted, backups won’t save your site from getting hacked. Nonetheless, they are an absolutely mandatory thing to have in case things go wild!
Backups are invaluable. If you have a recent backup of your site then you will be able to restore it back to normal no matter what bad thing might happen.
Two of the best methods to have this taken care of:
- through a free plugin – WordPress Backup to Dropbox – it takes your files and database contents, and stores it in your Dropbox account. Everything done on autopilot once a day; or:

- through VaultPress – a more feature-rich solution (a paid one; starts at $99 / year).
9. Choose the best web host you can afford
Right up front I have to be honest with you and admit that $5 / month web hosts aren’t much good.
I, for instance, once had my server infected by malicious code while running on a cheap $5 / month hosting plan. My site, my domain, and my WordPress were not even involved in the breach. It’s the server itself that got hacked.
Lesson? Don’t save money on your server plan. Always go for the best web hosting service that you can afford.
Some quality recommendations:
10. Only download plugins and themes from known sources
Accidental vulnerabilities, let’s name them that way, aren’t the only thing that can bite you.
There are also intentional vulnerabilities.
For instance, if you get a plugin from a shady source, it might feature source code designed specifically to hack your site. In that case, by getting the plugin, it’s you who’s effectively hacking your own site.
The same thing goes for themes.
How to find quality plugins and themes?
The first places to go are the official theme and plugin directories at WordPress.org. The downloads there don’t feature deliberately dangerous code.
When it comes to premium themes and plugins, you need to go by the seller’s reputation. ThemeForest and CodeCanyon are generally safe due to the lengthy and thorough review process for each new theme and plugin submitted there.
“THE ADVANCED TIER” of WordPress security
Do the following for extra security; still not particularly technical tasks:
11. Delete plugins you don’t use
As the MailPoet example teaches us (described above), you never know what surprises await inside your plugins.
Sometimes you’ll come across basic security vulnerabilities, other times something more serious.
Either way, to save yourself from trouble some more, simply remove all those plugins that you don’t use. Keeping them inactive won’t cut it. Remember that the source files of those plugins are still on your server.
So create a new habit, instead of just deactivating the plugin you’re not using at the moment, delete it completely.
12. Reduce your overall number of plugins
Apart from getting your plugins only from safe sources and known developers, and deleting the plugins you don’t use, you can also reduce the overall number of plugins you have installed.
And I’m not talking about just deleting stuff at random and losing good functionality.
Instead, try using plugins that replace other plugins with their functionality.
Here’s an example. Jetpack – a well-known plugin from team Automattic – can successfully replace a handful of other plugins that you might be using right now. For instance, some of the things Jetpack can give you:
- contact forms,
- image galleries and carousels,
- social media buttons,
- mobile theme,
- links to related posts,
- site stats, and more.

13. Use a security plugin
Security plugins are basically what the name suggests they are… Via various methods, they help your WordPress blog stay safe.
This is often done through database scans, firewall protection, file permission control, and a range of other things (let’s not get into the technical details).
Here are the most popular security plugins:

The great thing about them is that, very often, they work on autopilot, so you don’t need to necessarily understand what’s going on under the hood.
(Note. It’s best to use just one of such plugins, to avoid any software conflicts.)
14. Protect your site against brute force attacks
Brute force attacks are a different kind of animal.
Basically, if someone wants to mess things up on your site, they have two possible paths:
- the surgical attack – where they meticulously look for a vulnerability, and then explore it with laser precision,
- the brute force attack – where they simply attempt to guess your password multiple times until successful, which often means millions of tries in a row.
The best way to protect yourself from the latter used to be a plugin called BruteProtect. But as of August 2014, BruteProtect has been integrated into Jetpack (mentioned above).
15. Use CloudFlare
CloudFlare is a really mysterious solution for me. And what’s mysterious about it isn’t the fact that it’s very effective at what it does, but that most of the goodies are available for free.
In short, CloudFlare routes all traffic coming to your site through a network of servers. Those servers let in only genuine people who want to read your content, and bounce anyone who’s suspicious. Check out their “features” page to get a better understanding.
16. Monitor for malware
Malware is an umbrella term (Wikipedia says) that refers to various forms of intrusive software, including malicious web scripts – the stuff that can attack your WordPress blog.
… I hate malware. I’ve had malware one time on my site and it wasn’t fun.
And the sad thing is that you don’t find out that “you have malware” until it’s basically too late and the damage’s been done. Oh, and Google already dropped my site from the rankings at that point.
The best way to save yourself from similar trouble is to use a solution that scans your WordPress site constantly, and lets you know whenever anything shady is going on.
Two possibilities:
17. Perform a theme check
When you’re thinking about changing your theme, or getting a theme for a new site, start by performing a theme check with this plugin.

It will let you know if the theme follows all the latest WordPress standards and recommended code practices. This is a great way to find out if the developers really knew what they were doing.
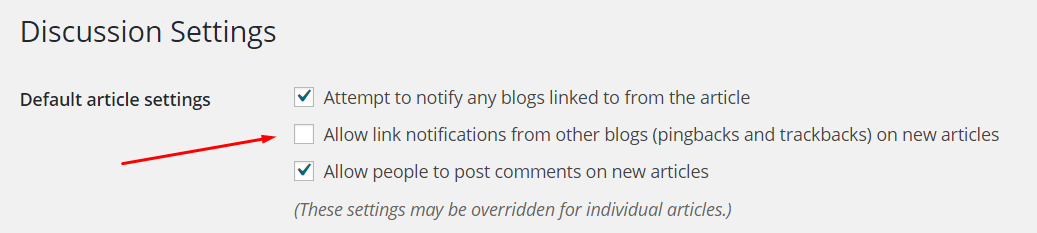
18. Block pingbacks and trackbacks
Setting the (questionable these days) usefulness of pingbacks aside, one more nail to their coffin is that pingbacks can be used for DDoS attacks. The Sucuri team shed some light on this a while ago.
Consider disabling pingbacks on your site. This can be done in Settings > Discussion. Just deselect this box:
“THE PRO TIER” of WordPress security
This PRO tier doesn’t get into much detail for each security measure it lists. I figured that since you already know your way around WordPress, just general headlines will be enough to get you in the right direction.
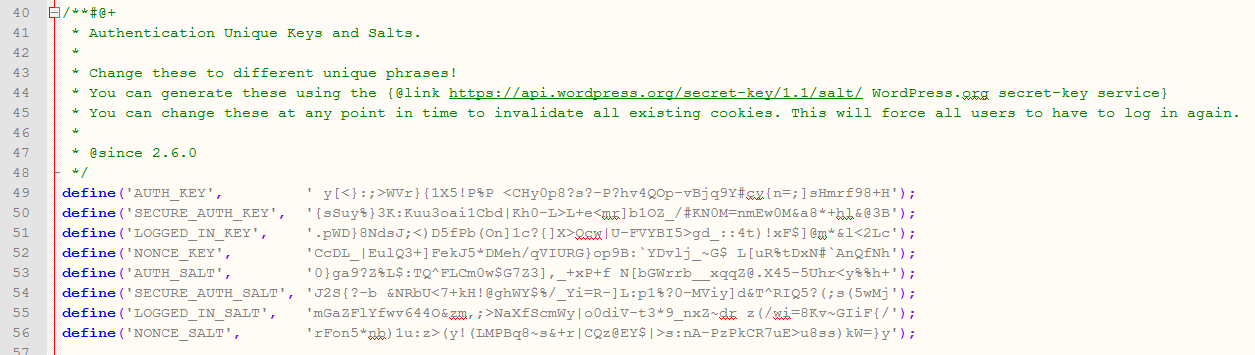
19. Generate new WordPress security keys
WordPress Security Keys handle the encryption of information stored in the user’s cookies. To make things secure, the keys need to be generated randomly for each WordPress install. Find them in the wp-config.php file.
20. Change your database prefix
The default database prefix for WordPress sites is “wp_”. If you change it, you’ll automatically make any SQL injection attack attempts way harder. Find this in the wp-config.php file.

21. Use .htaccess protection
.htaccess is a file that can have a huge impact on your overall site security. Either use plugins, or craft it manually according to the best practices.
22. Disable XML-RPC
XML-RPC has been turned on by default since WordPress version 3.5. However, occasionally, there are some problems with it.
Even recently, a new XML-RPC bug was discovered. This particular one made it possible for your site to be attacked via brute force.
Consider disabling XML-RPC altogether if you’re not using it for anything. For instance, delete the xmlrpc.php file.
23. Disable PHP error reporting
In itself, PHP error reporting is a good debug tool when building a new PHP app/website. But if enabled on a live site, in case of an error occurring, your whole server path gets displayed on the screen. This is a piece of info that’s rather valuable to hackers.
Consider disabling error reporting.
24. Track what’s going on in your dashboard
This is really useful if you have a number of users working in your dashboard (multi-author blogs).
Basically, having a handy log that records everything that’s going on in the dashboard can never hurt you. You can use the WP Security Audit Log plugin for this.
25. Pay attention to what Google Search Console (GSC) tells you
(Note. You might know GSC by its former, more familiar, name – Google Webmaster Tools.)
GSC is very useful when it comes to letting you know about malicious things going on with your site.
When my site got hacked for the first time, it’s GSC that notified me what was going on.
The lesson is simple; whatever site you have/manage, hook it up to GSC. It costs nothing and can bring huge benefits.
26. Read Sucuri
You may have noticed that I mentioned Sucuri and the Sucuri blog a handful of times in this post. It’s no accident.
The Sucuri guys are always on the lookout for new vulnerabilities, and very often it’s they who report on new problems before anyone else notices them.
Want to stay safe? Simply subscribe to their blog and read their reports.
27. Delete plugins that have been reported as being unsafe
Apart from the plugins you don’t use (described earlier), you should also act quickly whenever a plugin you use gets reported as being unsafe.
Of course, checking the security level of every plugin manually prior to installing it is beyond what any sane person is willing to do, but there are shortcuts.
For instance, some websites publish regular reports covering the latest WordPress vulnerabilities, including issues found in popular plugins. One of those websites is the aforementioned Sucuri, the other is this one.
(Just to motivate you some more to take this step; did you know that plugin issues account for 54% of all vulnerabilities found on WordPress blogs and sites?)
28. Use SSL
SSL is a technology allowing you to encrypt the connection between your web server and your visitors’ browsers. This increases the security of the whole experience, purely because all data being transferred can’t be easily read by third parties.
Enabling SSL for your site isn’t a five-minute deed, though. First, you need the right web host. Then, you need to get the SSL certificate itself. And finally, you need to integrate it with your WordPress site (plugins for that; e.g. Verve SSL or WP Force SSL).
Conclusion
Whew! We’ve covered a lot of ground here. I hope you’ll use these tips to make your WordPress blog more secure … effectively shutting the door on hackers and shady malware scripts.
But maybe there’s something I’ve missed here? Do you know of any other security measures that should be taken on a WordPress site or blog?

